Your operations team works to ensure all the processes in a company run smoothly. Nothing takes the steam out of the sails of a brand more than being victim to some type of cybersecurity hacking event. If you want your brand to keep humming along, you’ll want to be aware of some of the top phishing scams currently running the rounds.
From hackers to bored teenagers to competitors to disgruntled former employees, there are many different people who might want to get into your business’ network and create havoc. Your job as the operations team is to work alongside IT and make sure they don’t.
Which Businesses Are at Risk of Phishing Scams?
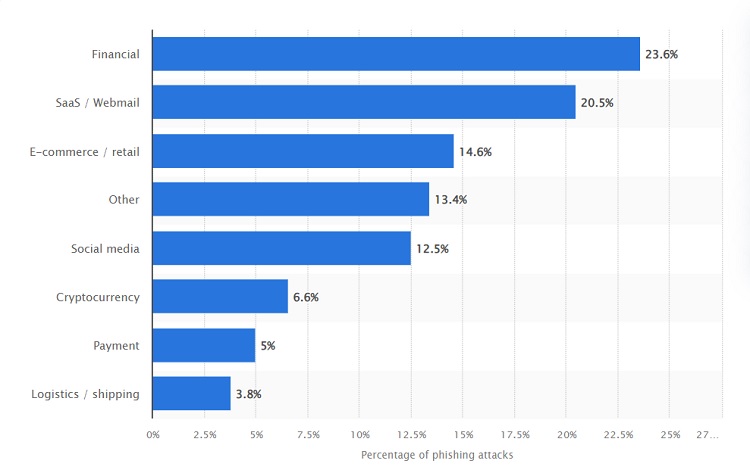
Source: https://www.statista.com/statistics/266161/websites-most-affected-by-phishing
Statista reports the financial sector is the most frequently impacted industry hit by phishing scams with 23.6% of the attacks hitting businesses in that category. Other popular targets include software as a service, e-commerce and social media.
Although your business may be more frequently targeted if you fall into one of those groups, any business can fall victim to a phishing scam at any time. It’s vital you remain aware of the current top phishing scams and spend time training employees to recognize them and avoid them.
Here are the top phishing scams your operations team need to be aware of and watch out for:
1. Fake Websites
Although not quite as common as email phishing messages, fake websites can be one way hackers gain access to your information. Train your employees to always check the address bar and ensure the name matches the name of the real website.
Phishing scams often try to get a domain name close to the name of the actual site. For example, if they wanted to pretend to be Amazon, they might take out a name such as Anazon.com. They often change just a single letter to try to trick the user.
2. Disaster Scams
Disaster scammers often use tragedies such as flooding, wildfires or tornadoes to try to trick people into sharing sensitive information and steal their money. While a natural disaster may not be what you initially think of when trying to avoid phishing scams, a natural event could happen almost anywhere to any business.
Make sure you’re aware that not every company approaching you is upfront and honest. Check and recheck references. Never pay upfront before a company completes work or share sensitive information you’d normally protect from outsiders.
3. Email Attacks

Source: https://www.addictivetips.com/vpn/phishing-statistics-forecasting
In a recent survey, business leaders shared their concerns over employees recognizing scams when they come their way. Around 55% were not confident workers would recognize email phishing attempts. About 66% said their employees probably wouldn’t spot other scams.
Email is one of the most common ways scammers try to gain access to login credentials and personal information. Your operations team would be wise to invest time and training into ensuring employees understand what phishing scams look like.
4. Spear Phishing
The attacker in this type of scam uses information they have about the employee or employer to gain the person’s confidence and get them to share sensitive details. For example, a former employee that left on negative terms may use their knowledge to try to get current login credentials.
They might send an internal memo or email to one or more employees. The email might even be designed to look as though it’s from someone else, such as the CEO of the company. Once the person shares the information, the hacker is into the system.
Set company policies where you never send login credentials via a message or email. Train staff to always verify the person they think sent the message actually did. Set up a process where anyone asking for login info be directed to go through IT or human resources instead. Such policies take the decision making out of the employees’ hands and help protect the company from invasion.
5. Unauthorized Logins
During the last few years, the number of cyberattacks grew at an unprecedented pace. With more people doing business online, working from home and companies getting in the cloud, there are more opportunities than ever before for cybercriminals to attack.
Making sure you put things behind a secure socket layer and encrypting personal details is a great start to protecting your information and your clients’ personal details. If you aren’t sure how safe your site is, enlist the help of a security professional.
Some hackers go to your website and try to login. They send out thousands of attempts, trying common default logins, such as “admin” or “password.” Even if they aren’t successful at getting into your website or system, they may cause your server to crash from the sheer volume of attempts.
What if they had some login credentials from an old account? Perhaps an employee left their computer up at Starbucks and a scammer grabbed their login data. If your operations team doesn’t immediately remove employees who leave from the system, you should do that today. You don’t want to let people who don’t actually work for you anymore into your systems.
6. Smishing

Source: https://www.marketingcharts.com/digital/mobile-phone-117548
Most operations teams and employees now own a smartphone and may use it for business purposes. Studies show about 85% of adults in the US own a smartphone. As more people turn to their digital devices for everything from entertainment to business, a whole new form of scam appears to be gaining traction.
Mobile phone SMS phishing, or smishing, is on the rise. The person receives a text that looks as though it’s from a company. It might say they need to authenticate their login with a particular company, for example. However, when they click on the link, they’re taken to a dummy site that collects their credentials and uses them to hack into the system.
Train your workers to never click on an SMS link. They should always go directly to the website. Ask your team and everyone who works for you to install antivirus software on their phones. Be smart and aware to avoid a hacking attempt.
Watch the News
If scammers spent one-tenth the time working as they do on coming up with new scams, they’d likely make an excellent living. Unfortunately, figuring out how to phish their way into your company databases is a game for many people. To stay on top of phishing scams and protect your sensitive data, watch the news. See what types of scams other companies fell for, particularly those in your industry. Being aware of the latest phishing endeavors gives you an opportunity to combat them before they become a problem.
About the Author: Eleanor Hecks is editor-in-chief at Designerly Magazine. She was the creative director at a digital marketing agency before becoming a full-time freelance designer. Eleanor lives in Philadelphia with her husband and pup, Bear.
